Estimated reading time: 8 minutes
Introduction
The Bring Your Own Device (BYOD) trend continues to accelerate, with the market growing from $76.9 million to $103.11 million between 2024 and 2025 alone. As more organizations embrace BYOD policies to increase flexibility and reduce costs, they face a critical challenge: balancing robust security measures with employee privacy concerns. Simplemdm
This article explores the inherent tension between security and privacy in BYOD environments, providing guidance for business leaders on how to implement appropriate policies that protect corporate data without being unnecessarily invasive of employee privacy.
Understanding the Fundamental Tension
At the heart of every BYOD implementation is a fundamental conflict: organizations need to secure their data and systems, while employees expect reasonable privacy on their personal devices. This tension increases as security measures become more comprehensive and potentially intrusive.
The Security Imperative
Organizations face legitimate security concerns with BYOD, including:
- Data leakage through unsecured personal devices
- Malware and cyber threats entering corporate networks
- Lost or stolen devices containing sensitive information
- Compliance violations with industry regulations
- Unauthorized access to corporate resources
The Privacy Expectation
Employees using personal devices for work have reasonable privacy expectations, as they often store highly personal information including photos, messages, health data, financial information, and private communications on these same devices. Techtarget
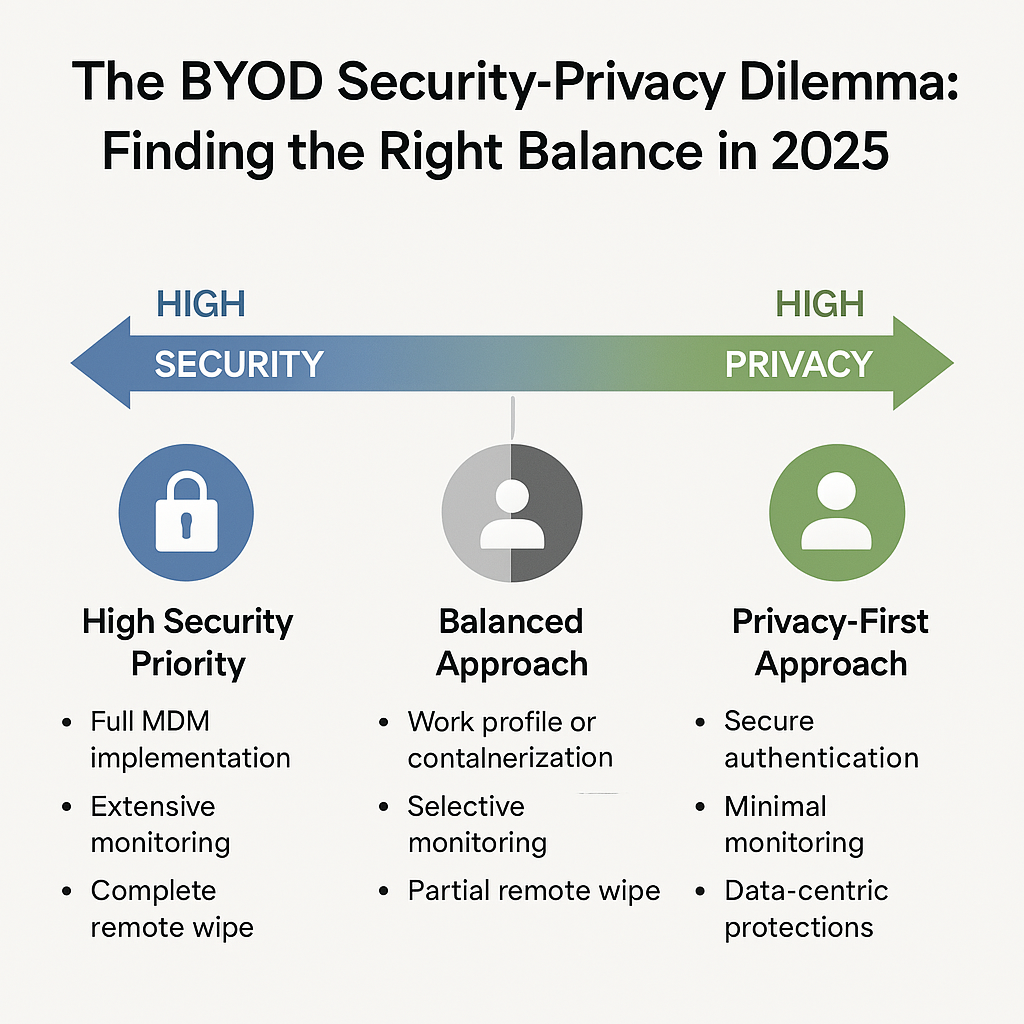
The Security-Privacy Spectrum
Understanding where your organization falls on the security-privacy spectrum is essential for developing appropriate BYOD policies. Here’s how different approaches balance these competing interests:
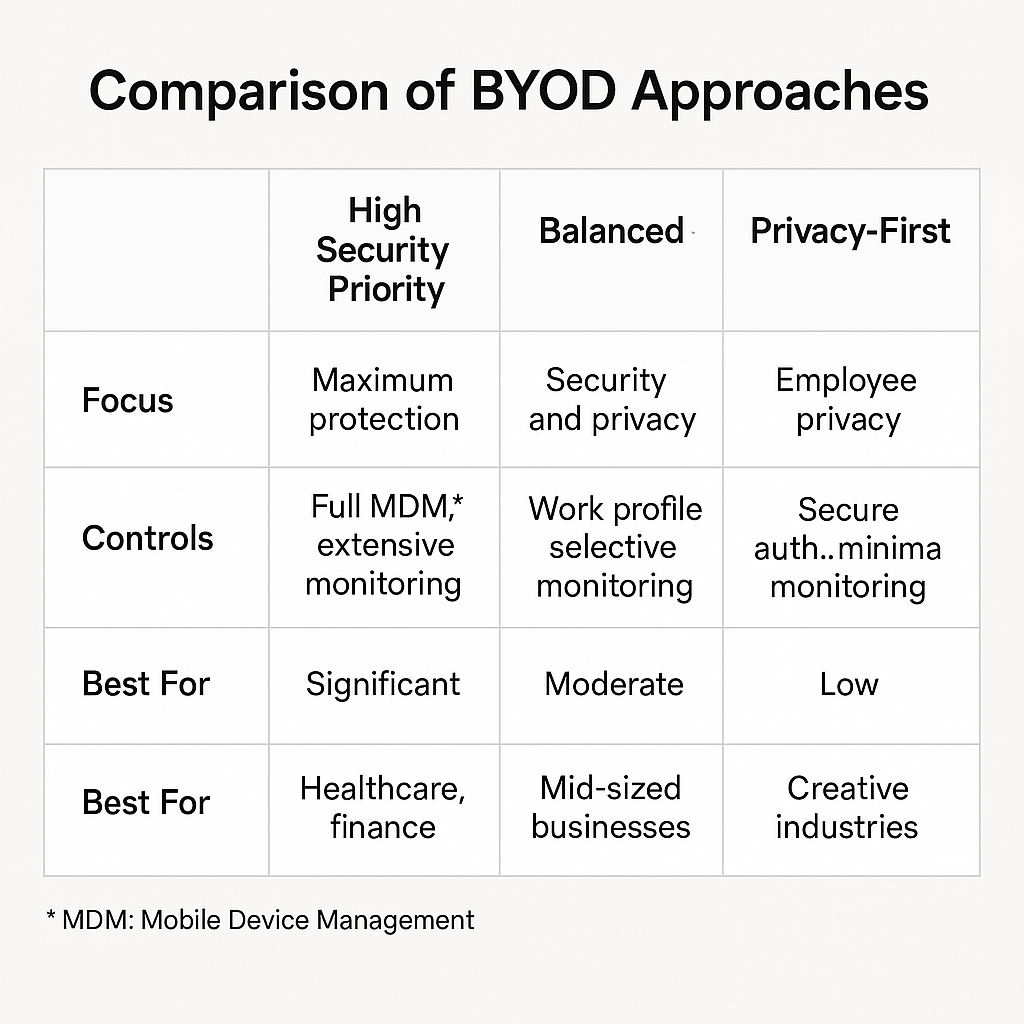
High Security, Low Privacy
Characteristics:
- Comprehensive Mobile Device Management (MDM) with full device control
- Ability to monitor all device activities, including personal usage
- Remote wipe capabilities for the entire device
- Strict application controls and prohibitions
- Extensive logging and monitoring
Benefits:
- Maximum protection of corporate data
- Comprehensive compliance capabilities
- Immediate threat detection and response
- Complete control over corporate resources
Drawbacks:
- Significant employee privacy concerns
- Potential legal issues in some jurisdictions
- Employee resistance and dissatisfaction
- Blurring of work-life boundaries
- Possible decreased productivity due to restrictions
Balanced Approach
Characteristics:
- Containerization to separate work and personal data
- Work profile isolation on personal devices
- Limited monitoring of only work-related activities
- Selective remote wipe of only corporate data
- Reasonable application controls focused on work functions
Benefits:
- Strong protection of corporate data
- Reasonable employee privacy preservation
- Compliance with most regulatory requirements
- Better employee acceptance
- Clearer boundaries between work and personal use
Drawbacks:
- Some security gaps compared to full control
- More complex to implement and manage
- May require more sophisticated technologies
- Some privacy concerns still exist
High Privacy, Low Security
Characteristics:
- Minimal controls focused only on access authentication
- No device monitoring or management
- Limited or no remote capabilities
- Few restrictions on device usage or applications
- Reliance on user education rather than technical controls
Benefits:
- Maximum employee privacy preservation
- Higher employee satisfaction and acceptance
- Simpler implementation
- Fewer legal concerns regarding privacy violations
- Clear separation of work and personal domains
Drawbacks:
- Significantly increased security risks
- Limited compliance capabilities
- Difficult to respond to security incidents
- Potential data loss with no recovery options
- Increased liability risks for the organization
Industry-Specific Considerations
Different industries have varying needs along the security-privacy spectrum:
Healthcare
Healthcare organizations must adhere to strict HIPAA regulations, requiring robust security measures to protect patient data while still respecting healthcare worker privacy on personal devices. Alwaysbeyond
Recommended approach: Containerization with strong work profile isolation and selective controls that protect patient data without monitoring personal usage.
Financial Services
Financial institutions face strict compliance requirements including SOX and various banking regulations that mandate strong controls over financial data.
Recommended approach: Advanced MDM with robust containerization, ensuring separation between personal and work data while maintaining strong security controls over financial applications and data.
Legal Services
Law firms must maintain attorney-client privilege while protecting sensitive client information on mobile devices.
Recommended approach: Work profile isolation with strict data-centric protections and limited monitoring that focuses on client data rather than employee activities.
Creative Industries
Design firms, marketing agencies, and other creative businesses may need more flexible approaches to support creative workflows.
Recommended approach: Focus on data-centric protections and education rather than strict device controls, emphasizing secure access to creative assets rather than device monitoring.
Technology Solutions for Balancing Security and Privacy
Modern technologies offer ways to balance security needs with privacy concerns:
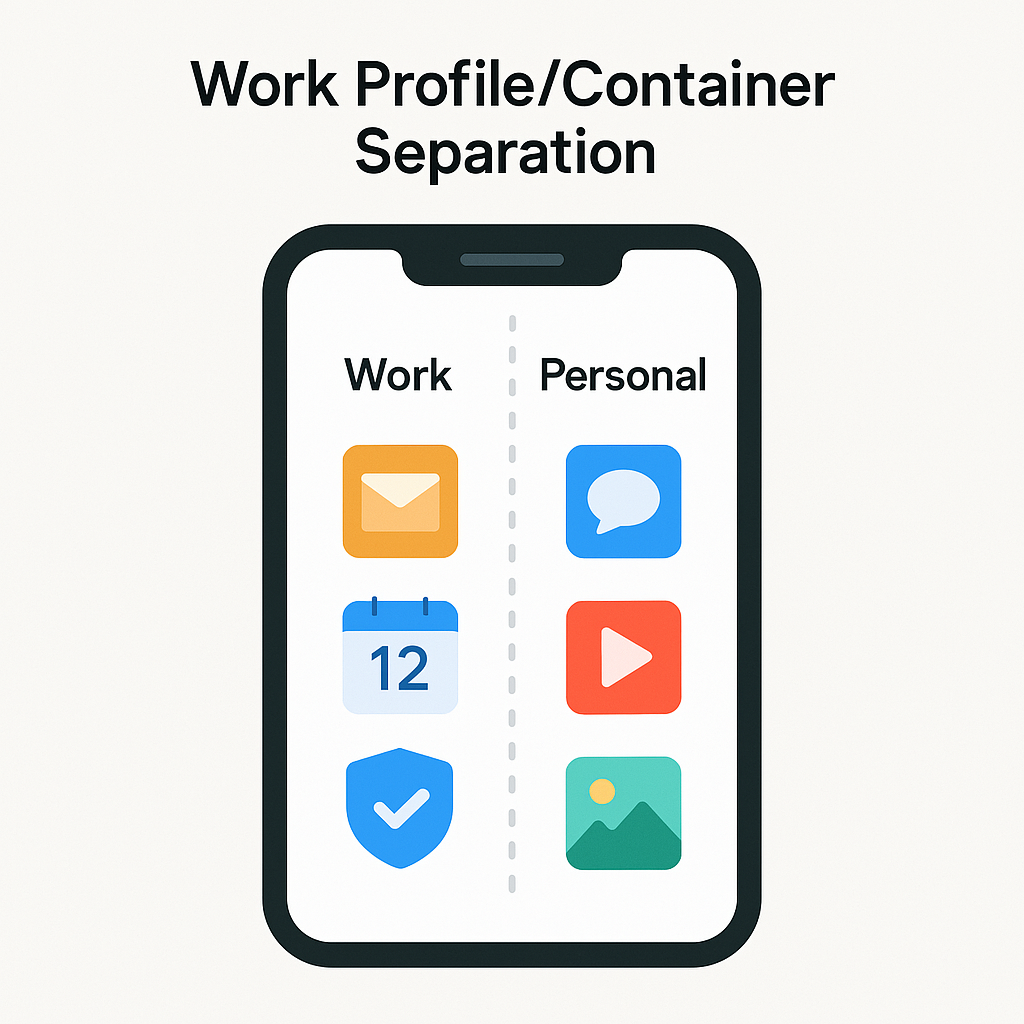
Work Profile Separation
Android devices offer work profile features that create a clear separation between personal and corporate data and applications, allowing management of the work profile without intruding on personal usage. Appaloosa
iOS User Enrollment
Apple’s User Enrollment allows employees to use a corporate identity alongside their personal one, enabling MDM solutions to manage corporate data without accessing personal information. Appaloosa
Mobile Application Management (MAM)
MAM solutions focus exclusively on managing corporate applications rather than the entire device, providing security for company data without affecting personal usage. Simplemdm
Containerization
Containerization divides the device into separate protected environments, each with different passwords, security policies, and data. This allows employees unrestricted personal use while maintaining security for corporate resources. Perception Point
Legal and Ethical Considerations
Organizations must consider legal implications of their BYOD policies:
Privacy Laws
If a company’s BYOD policy doesn’t obtain consent before accessing an employee’s device, the organization may face legal consequences under privacy laws and constitutional protections like the Fourth Amendment. Infosecinstitute
Data Protection Regulations
BYOD practices can lead to risks including data breaches and violations of federal privacy laws, making it essential to implement comprehensive written policies and appropriate technical controls. Wakeforestlawreview
Employee Consent
Clear documentation of consent is crucial, outlining what the organization can access, what security measures will be implemented, and what happens in security incidents. Appaloosa
Creating a Balanced BYOD Policy
A well-designed BYOD policy should address both security and privacy concerns:
1. Define Clear Boundaries
Explicitly state what the organization can and cannot access on personal devices. Most MDM solutions allow administrators to define appropriate policies for corporate-owned versus BYOD devices, offering different levels of control based on how the device is enrolled. Techtarget
2. Implement Appropriate Technology
Choose technology solutions that provide necessary security while respecting privacy:
- For high-risk environments: Use containerization with work profiles
- For medium-risk environments: Implement MAM with selective controls
- For low-risk environments: Focus on secure authentication and data-centric protections
3. Obtain Informed Consent
Ensure employees understand and consent to the BYOD policy before implementing it, whether it appears in an employment contract, orientation materials, or when installing MDM software on personal devices. Privacyrights
4. Limit Data Collection
Only collect the minimum data necessary for legitimate security purposes. Avoid collecting personal information, browsing history, or non-work-related data.
5. Provide Transparency
Clearly communicate what is being monitored and why, helping employees understand the security rationale behind any controls implemented on their devices. Appaloosa
6. Create Data Separation Procedures
Establish clear procedures for separating personal and corporate data, especially when employees leave the organization or devices are lost.
7. Train Employees
Provide comprehensive training on both security best practices and privacy protections, helping employees understand both their rights and responsibilities.
Real-World Implementation Examples
Case 1: Healthcare Provider
A healthcare network implemented a containerized approach that created a completely separate work environment on employee devices. The container had strict controls for HIPAA compliance, but the organization had zero visibility into personal usage outside the container. The result was strong security for patient data with full preservation of employee privacy.
Case 2: Financial Services Firm
An investment firm used a hybrid approach with MAM for most employees and full MDM for high-risk roles handling sensitive financial data. Employees could choose which level of management fit their role, with appropriate compensation for those accepting higher security controls. This tiered approach balanced security needs with privacy preferences.
Case 3: Technology Startup
A software startup implemented a minimal BYOD policy focused primarily on secure authentication and data access controls rather than device management. By focusing security efforts on protecting their systems rather than controlling devices, they maintained high employee satisfaction while still protecting critical intellectual property.
Best Practices for Different BYOD Policy Levels
Basic Level BYOD
Security measures:
- Password requirements
- Secure authentication for corporate resources
- Basic data encryption for work information
- Remote wipe capabilities for corporate data only
Privacy protections:
- No monitoring of personal activities
- Clear separation of work and personal data
- Limited IT visibility into device usage
- Employee control over most device settings
Intermediate Level BYOD
Security measures:
- Work profile separation or containerization
- Application controls for work applications
- Network monitoring for corporate connections
- Enhanced authentication requirements
- Selective remote management capabilities
Privacy protections:
- Monitoring limited to work profiles only
- Personal data explicitly excluded from management
- Transparency about what can be accessed and when
- Selective wipe capabilities that preserve personal data
Advanced Level BYOD
Security measures:
- Comprehensive MDM implementation
- Application whitelisting/blacklisting
- Data loss prevention controls
- Security event monitoring and response
- Full device encryption
Privacy protections:
- Clear consent for enhanced monitoring
- Detailed privacy impact assessments
- Legal review of privacy implications
- Compensation or alternatives for privacy concessions
- Regular privacy audits and policy reviews
Conclusion
Finding the right balance between security and privacy in BYOD policies is not a one-size-fits-all proposition. Organizations must carefully consider their security needs, regulatory requirements, employee expectations, and technical capabilities.
By implementing appropriate technologies, clear policies, and ongoing education, organizations can create BYOD environments that protect corporate assets while respecting employee privacy. The key is transparency and proportionality—implementing security measures that address real risks without unnecessarily intruding into employees’ personal lives.
As BYOD continues to evolve in 2025 and beyond, the organizations that succeed will be those that view security and privacy not as competing interests but as complementary aspects of a healthy digital workplace.